General overview of the system
Benefits of Unix
- The system is written in high level language “C” which makes it easier to read understand and update. It off-course is little slower in comparison to what written in assembly language but the advantages are far greater and possibilities are endless.
- Complex programs can be built on simple programs on unix systems.
- It has hierarchal file system which allows easy maintenance and efficient implementation.
- It has consistent format for files. The files are stored as byte streams which makes it easier for the programs to use files.
- It provides simple and consistent interface to the peripheral devices.
- It completely hides the machine architecture from the user which makes it easier for the programmers to write programs independent of hardware.
System Structure
The unix system can be viewed as the set of layers. The lowermost layer is the hardware layer which is not the part of the unix operating system. The operating system is called the system kernel or the kernel.
Kernel is the layer where the actual operating system code and functionality resides. It is in complete isolation from the user programs. This makes it easier for the programs to be ported onto other system provided the kernel are same.
If a user program want to perform any task it can do so by talking to the kernel. The programs interact with the kernel by using the system calls. The system calls instruct the kernel to do various operations.
Other user programs can be built on top of the lower level programs using these lower level programs and system calls.
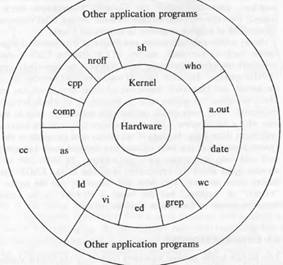
User perspective – The file system
The characteristics of unix file system are
- A hierarchal structure.
- Consistent treatment of data
- Ability to create and delete files
- Dynamic growth of files
- Peripheral devices are also treated as files
The file system is organized as a tree. The root node is called “root” and is denoted by “/”. Every non leaf node in this structure is a directory and every leaf node is a file/special device file.
The name of the file is given by the path name.
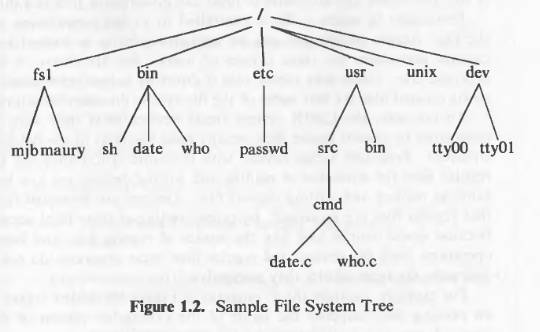
A full path name starts with the root directory i.e. a slash character and specifies the file that can be found by travestying the tree. Some examples of paths could be “/etc/passwd”, “/bin/who” and “/usr/src/programs/test.c”.
The path that starts from the root directory is called the absolute path. Alternatively we can give path of any file relative to any other directory. This path will be called relative path.
The files are just stream of bytes it is up-to the program to interpret these bytes. Directories are also files i.e. a stream of bytes but the operating system program knows how to interpret them as directories. Example program could be “ls”
Permission to any file is governed by the file access permissions. Access permissions are set independently for read, write and execute. These permissions are set independently for the file owner, file group and everyone else. Access permission looks like
rwx-rwx-rwx (We will see more of this in later chapters)
Unix treats devices as if they are files. Every device is treated as special files and occupy position in the file system. Programs can access devices using the same syntax as if they were accessing files. Syntax of reading and writing on devices is more or less same as reading and writing regular files. Devices are protected in the same way as files i.e. using access pemissions.
User perspective – Processing environment
A source code is our program source code, an executable file is the program for our source code and the process is the instance of our program in execution. Many processes can execute simultaneously in uix. (Multiprogramming or multitasking). Also many instances of one program can run simultaneously. Each instance of this program is one process. Various system calls allows control of the state of the process. The state of a process indicates its status at a particular time. The process state could by any one of the following.
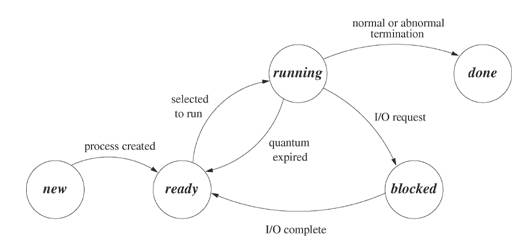
Process state information along with other useful information is stored in a process control block. Every process has its own process control block or PCB.
Unix shell allows three types of commands.
- An executable file created by compilation of our source code.
- An executable command that contains a sequence of shell commands.
- An internal shell command.
The shell, usually, run the commands synchronously. However these commands can also be run asynchronously.
User perspective – building block primitives
Unix allows user to write small programs, in a modular way. These programs can be used as building blocks to build the complex programs.
Unix has three standard files:
- Standard input file
- Standard output file
- Standard error file
Typically when we run shell our terminal (monitor) is serving as these three files. (remember devices can be treated as files).
One primitive building block available to the shell user is the redirect I/O. for example
ls
this command list down all the files in the current directory.
ls > output
this command will send this list of files to a file named “output” instead of the terminal.
The second building block primitive is the PIPE. Pipe allows a stream of data to be passed from processes. There is one reader process and one writer process.
ls | more
Operating system Services
The kernel layer provides various oerations on behalf of user processes. Some of the main services provided by the operating systems kernel are:
- Process control: controlling the creating, termination and suspension of processes.
- Scheduling processes: Since many programs can execute simultaneously in unix the process scheduling is also done by the kernel.
- Main memory management: allocating main memory to the user programs and protecting the memory region where kernel is running. Also, protecting the memory region of one process from another process.
- Virtual memory: managing the swap device and handling the swapping system. Controlling the pages in the paging system(memory allocation)
- Secondary memory management: Managing the secondary storage for the efficient and timely retrieval and storage of data.
- Peripheral devices: kernel controls the peripheral devices such as terminals, disk drives and network devices.
Assumptions about the hardware
When a process executes on unix it executes on two levels or we can say it executes in two modes.
- User level
- Kernel level
Processes in user mode can assess their own instructions but not the kernel instructions or the instruction of other processes. On the other hand processes in kernel mode can access kernel data and instructions as well as user data and instructions.
The system calls can only be executed in the kernel mode. If a user process running in user mode make a system calls the process shifts from user mode to kernel mode and then the kernel services the request and the system comes back to the user mode after the request is serviced.
Interrupts and exceptions
The devices can interrupt the CPU anytime asynchronously. On receiving the interrupt the kernel saves its current context(whatever it was doing) and jumps to service that interrupt. After the kernel is done servicing the interrupt it reloads its context and resumes whatever it was doing.
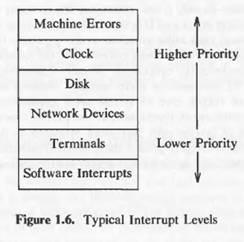
There might be a possibility that kernel is servicing one interrupt and another interrupt may occur. So whether or not to service that interrupt and stop whatever kernel was doing is decided by the interrupt priority(or interrupt levels). If a high priority interrupt occurs the kernel stops the previous one and jumps onto second. If a lower priority interrupt occurs the kernel will not stop what it was doing and that interrupt will have to wait. In other words the lower priority interrupt is blocked if kernel is servicing some high priority interrupt.
An exception occurs when a process does something unexpected. Exceptions are different from interrupts they occur as events. If an interrupt occurs in the middle of instruction, that instruction will be restarted after handling the exception. If the exception is not caused by the instruction but because of some other reasons and between two instructions then the next instruction is processed after handling the exception.
Memory management
The unix kernel is in main memory and the user programs are also in main memory so The operating system resides in the lower memory. User processes execute in the higher memory. There is always a possibility that user processes may try to access the lower memory either accidentally or intentionally thereby causing loss of operating system code and data. to prevent the user programs to corrupt the kernel memory the memory management is also done by the unix kernel.